
SOCCER Project
Recent events such as the global pandemic, geopolitical tensions, and the introduction of new internet technologies have elevated cybersecurity to the second most important risk worldwide. The project "Security Operation Centres Capacity Building for European Resilience - SOCCER" was established in response to the European call DIGITAL-ECCC-2022-CYBER-03-SOC - Capacity building of Security Operation Centres (SOCs). This project brings together a consortium of cyber and technology experts from Germany, France, Hungary, and Romania.
Over the course of 36 months, our proposal aims to:
- Develop and implement cutting-edge technologies for secure data access (Security Hub) and the sharing of threat intelligence signals (TIS) across European entities, enhancing the capacity to monitor and detect cyber threats.
- Interconnect and strengthen advanced Security Operation Centres (SOCs) ecosystems in Germany, Hungary, and Romania, with the goal of enhancing cybersecurity resilience at both national and EU levels.
The use of state-of-the-art AI, machine learning capabilities, and investment in common infrastructures will enable more efficient and rapid sharing and correlation of threat intelligence signals. Through a focus on cybersecurity upskilling, sharing best practices, and developing a European-wide, human-centered AI solution, the consortium will build capacities that guarantee trustworthiness and technological sovereignty, providing a competitive advantage on a global scale.
The consortium approach aligns with European cybersecurity strategies and the standards of the following member states:
- NIS Directive, Cybersecurity Act, Regulation on the European Cybersecurity Competence Centre (ECCC) and the Network of National Coordination Centres
- Joint Cybersecurity Unit, German IT Security Act 2.0
- German Federal Office for Information Security (BSI) and its Regulation on critical infrastructures (KRITIS), GDPR, and ISO standards
Threat Intelligence Sharing Platform
The Signal Iduna Group, Trout Software, Orange Romania, and Sztaki are working together to create a common repository for cyberattack data, known as the Threat Intelligence Sharing Platform. This platform collects a unique combination of key behavioral characteristics and detection indicators that describe cyberattack pathways within IT systems.
Leveraging available sources of Indicators of Compromise (IoC), the repository expands these indicators by offering complete kill chains, describing the tactics, techniques, and procedures involved at each step. The kill chains also include artifacts for automated identification, as well as malware samples and network records in a digitally secured zip format.
The IoC data is represented using industry-standard YARA and Snort rules, with network data samples provided as PCAP files and malware artifacts as binary code. The metadata for kill chains is encoded in an innovative ATT&CK-over-STIX format: STIX characterizes object identities and relationships, while the ATT&CK ontology describes the tactics, techniques, and procedures (TTPs) used in each kill chain step. Focusing on TTPs is recognized industry-wide as a robust detection and defense strategy against evolving cyber threats.
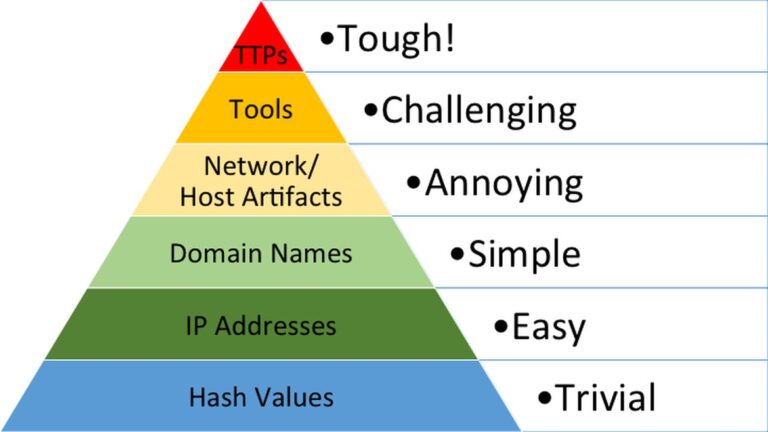
Figure 1: David J. Bianco, Pyramid of Pain (2014)
By providing a repository of well-documented kill chains in a format compatible with existing tools, the platform strengthens collaboration between consortium members (objective #2 of the project) and potentially between European Security Operation Centers (SOCs) in the future. It serves as a neutral medium to describe attack patterns, enabling defenders to implement mitigations before an attack takes hold.
The data set will grow to multi-terabyte levels due to the binary nature of the files. Trout Software will initially collect the kill chains during repository creation, and all consortium members will contribute equally as SOCs are ramped up.
The Threat Intelligence Sharing Platform will facilitate knowledge sharing about cyber systems, support training for future cybersecurity analysts, and provide a foundation for evaluating the effectiveness of cybersecurity products and services (in line with the requirements of the Cyber Resilience Act). Using industry-standard formats and data from open research bodies, as well as research by consortium members, this platform will form the nucleus of a comprehensive database. The consortium also aims to extend database access to European institutions involved in cybersecurity training, including universities and commercial awareness programs.